Email encryption prevents sensitive information from reaching the wrong people. Outlook, the well-known email client, includes encryption to protect your messages. You will learn to encrypt emails in Outlook with clear steps from our guide.
Understanding Email Encryption
You need to grasp the concept of email encryption and its importance. Encryption turns plain text into coded format, unreadable without a decryption key. This keeps your emails safe from unauthorized access during transmission and storage.
Encrypting a Single Email
Encrypt one email in Outlook by following these steps:
- Compose Your Email: Draft the email, entering the recipient’s address, subject, and message content.
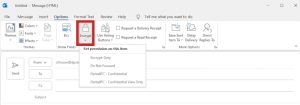
- Access Security Settings: Click the “File” tab, select “Properties,” and then “Security Settings.”
- Enable Encryption: Check the box labeled “Encrypt message contents and attachments.”
- Send the Email: Hit “Send” to transmit the encrypted email.
Encrypting All Outgoing Emails
Encrypt all outgoing emails for frequent handling of sensitive data, encrypt all outgoing emails:
- Access Outlook Options: Navigate to the “File” tab and click “Options.”
- Open Trust Center: In the Outlook Options, select “Trust Center,” and then “Trust Center Settings.”
- Enable Universal Encryption: On the “Email Security” tab, check “Encrypt contents and attachments for outgoing messages” under “Encrypted email.”
- Configure Additional Settings: Customize further by clicking “Settings,” like choosing a certificate or setting encryption levels.
Receiving and Opening Encrypted Emails
Decrypting an encrypted email requires a decryption key. You’ll usually get instructions on obtaining this key. Follow those steps to access your encrypted email content.
Limitations and Considerations
Outlook’s encryption offers basic protection, but it has limits. Both sender and recipient must use compatible email systems and encryption settings. Secure management of encryption keys is vital. Lost or compromised keys make emails unreadable. Pair email encryption with strong passwords, two-factor authentication, and regular updates.
Third-Party Encryption Solutions
Advanced needs might require third-party encryption tools. These often provide features like key management, self-destructing messages, and recipient authentication. Consider them for enhanced security.

Hi there! I’m John R. Steadman, if you want my services, my email is: [email protected]
I am a tech writer at ditii.com.
My passion lies in helping users recover their emails and understand the nuances of email creation and management. I strive to produce content that is both educational and user-friendly, ensuring readers can easily follow and implement my advice.
I enhance the visibility and reach of our content, providing effective solutions for common email issues.

